Category Archives: Network
How SSL WORKS
“Nothing is secure over Internet”
Internet does not ensure security always. It is almost a fact. So Users and Website owners are more inclined to make applications more secure over internet. They want a weapon to defeat the malwares, spywares, Trojans and many more belonging to this category.
When you send a request or sensible data to a website, it goes from your Local network through many routers and switches to ISP (Internet Service Provider) and finally to the destination server or website owner. It creates huge opportunities for the Man-In-The middle (MITM) to tamper or eavesdrop your sensible data particularly your credentials. With simple HTTP protocol we are just sending the data/hypertext in plain text format. Stealing your sensitive data would be as easy as snapping fingers for an attacker. HTTPS protocol makes it more secure by requesting and responding data on the top of SSL/TLS layer.
How SSL Works:
Secure Socket Layer (SSL) is used to ensure a secure connection between server and client. A third party, Certificate Authority, is used by this protocol to ensure that server and client are not fake to each other.
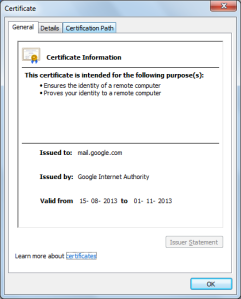
The certificate information for any website (www.gmail.com in this case) can be verified as given in the below screenshot.
To know the certificate one need to click on lock icon on the address bar of the website.
A certificate can be called as a digitally signed statement that binds the value of a public key to the identity of the person, device, or service that holds the corresponding private key. One of the main benefits of certificates is that hosts no longer have to maintain a set of passwords for individual subjects who need to be authenticated as a prerequisite to access.
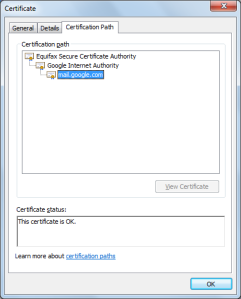
You can be acknowledged with the certificate authority and certificate path by opening certificate details page as given in the below screenshot.
This confirms that the Gmail page has been authorised by “Equifax Secure Certificate Authority”.
Steps explaining SSL handshaking
Let’s have a diagrammatic representation of how SSL layer works and how it makes sure that your data is safe.
- Client (Mostly a browser) sends a HTTPS request to the server for a Secure session between Client and Server. Client request for a SSL certificate to the server.
- Server Sends a SSL Certificate authorized from a third party vendor, Certification Authority Along with the SSL Certificate. It sends a Random Number or public Key to the Client. The digital signature on the certificate is someone vouching for the fact that a particular public key belongs to a particular individual or organization.
- Sever Sends a request to Browser for client certification. As both the parties need to identify each other.
- Browser checks the Server Certification. Now Browser understands that an Individual or an organization really exists in public record and can be trusted.
- Browser sends the SSL certificate to server with a Random number or public key. The digital signature prevents the Attackers/Snoopers from disguising as a client and providing their own public key.
- Server checks the client certificate. Now server is sure about the existence for an actual Client but not a snooper. The First level of security check is done.
- Client generates a Pre-Master Key. There are several methods to create Pre-Master Key. This is second layer of security for the transmitted data.
- Client sends an Encrypted data with server key.
[Message –> Private Key–> Encrypted Data]
- Both Browser and Server create Master Key with the Premaster Key and Public key from Server and Public Key from Client.
- Browser sends the encrypted data with the master key.
- SSL handshaking ended. Client sends a separate (encrypted) message indicating that the server portion of the handshake is finished.
- Server sends the encrypted key with the master key.
- SSL handshaking ended. Server sends a separate (encrypted) message indicating that the server portion of the handshake is finished.
In this way https ensures a secure connection and is more reliable mode of browsing the WebPages.
If you want to verify the https packets as secured ones, you need to run “Wireshark” tool on your client machine and browse any website with “https” in the URL. You can check the incoming packets in encrypted form ensuring the data as secured.
“Make your data secure, make your life safer”
Written By: – Chinmay Brahma, QA Engineer, Mindfire Solutions